Last year, the number of cyberattacks recorded was record-breaking, with a 50% increase in overall attacks per week on corporate networks compared to 2020. In fact, in 2021, the world witnessed one of the most serious vulnerabilities on the internet, with millions of attacks per hour attempting to exploit the Log4J vulnerability in what’s been dubbed a cyberattack pandemic.
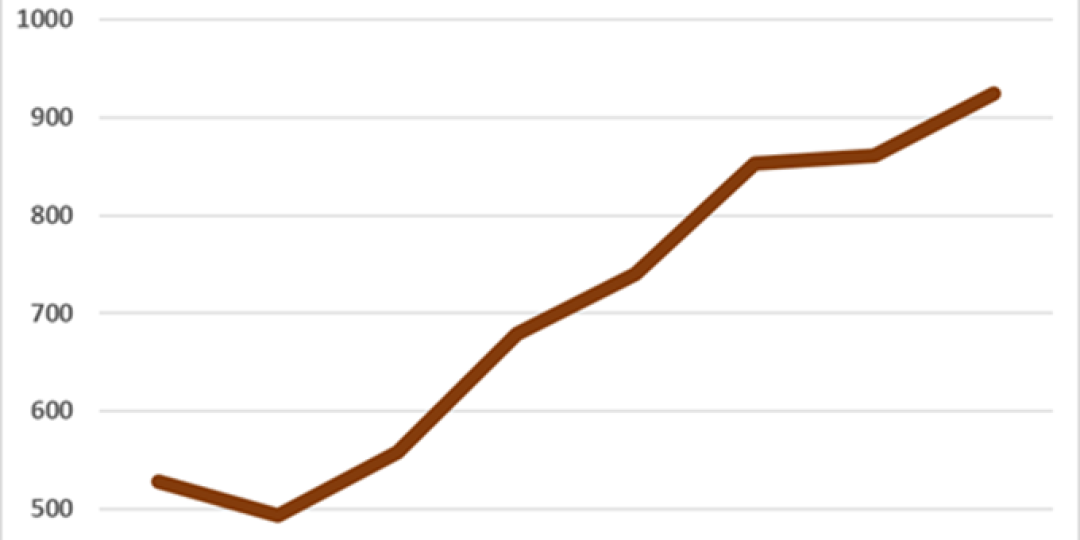
In October, Check Point Research reported a 40% increase in cyberattacks, with one out of every 61 organisations worldwide impacted by ransomware each week. By Q4, the upwards global trend continued, as the graph below shows, reaching an all-time peak by December, with 925 cyberattacks reported per organisation every week.
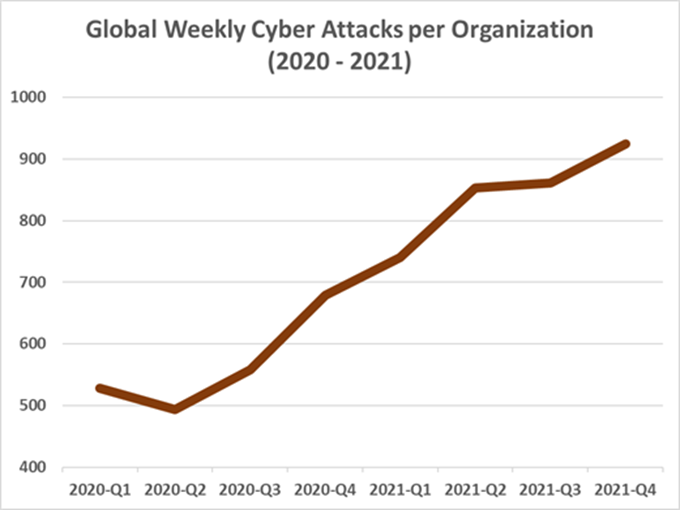
Africa most targeted region
Africa experienced the highest volume of attacks in 2021 across five surveyed regions, as the graph below highlights. Across the continent, an organisation had to contend with an average of 1 582 cyberattacks per week, which is a 13% increase from 2020.
The APAC region suffered the second highest volume of cyberattacks last year, with an average of 1 353 weekly attacks per organisation, followed by Latin America with 1 118 weekly attacks per organisation. The final two regions of Europe and North America recorded the least cybercrime with 670 and 503 weekly attacks per organisation respectively.
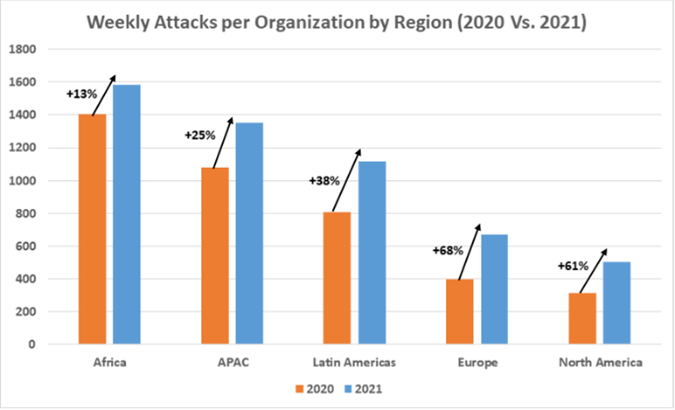
Education and research most impacted sector
Seeing a 75% increase in attacks compared to 2020, the education/research sector experienced the highest volume of cybercrime last year with an average of 1 605 attacks per organisation each week. Out of the 16 sectors surveyed per the graph below, government/military was the second most targeted, followed by communications, seeing a 47% and 51% increase respectively in weekly attacks per organisation in these sectors.
Six strategies to boost cybersecurity in 2022
The increase recorded last year in Gen V attacks – a combination of a wide breadth of threats, large scale attacks, and a broad attack surface – is alarming. Such attacks are the biggest challenge facing security practitioners, requiring effective measures to be put in place:
- Prevent attacks before they happen: a security architecture that enables and facilitates a single, cohesive protection infrastructure is essential, which is what Check Point Infinity delivers. This type of architecture provides faster, more comprehensive protection than an infrastructure comprised of pieces that don’t work together.
- Secure every attack surface and vector in your business: organisations need a single solution that provides broad cybersecurity coverage. This has become critical in today’s multi-hybrid environment where the perimeter is now everywhere. Email, web browsing, servers and storage are merely the basics. Cybersecurity should protect these and much more. Mobile apps, cloud and external storage are essential, so is compliance of connected mobile and endpoint devices, and your growing IoT-device estate. Workloads, containers and serverless applications on multi- and hybrid-cloud environments should always be part of the security check list.
- Apply security patches: cyberattacks penetrate networks by leveraging known vulnerabilities where a patch is available but has not been applied. Organisations must ensure that up-to-date security patches are maintained across all systems and software.
- Segment your networks: networks should be segmented, applying strong firewall and IPS safeguards between the network segments. This contains infections from propagating across the entire network.
- Educate employees on cybersecurity: Quite often, user awareness can prevent an attack before it occurs. Take the time to educate your users and ensure that if they see something unusual, they report it to your security teams immediately. User education has always been a key element in avoiding malware infections.
- Implement advanced security technologies: There isn’t a single silver bullet technology that can protect organisations from all threats and all threat vectors. However, there are many great technologies and ideas available – machine learning, sandboxing, anomaly detection, content disarmament, and many more. Each of these technologies can be highly effective in specific scenarios, covering specific file types or attack vectors. Two key components to consider are threat extraction (file sanitisation) and threat emulation (advanced sandboxing). Each element provides distinct protection, that when used together, offer a comprehensive solution for protection against unknown malware at the network level and directly on endpoint devices.
The statistics and data used in this report were detected by Check Point’s Threat Prevention technologies, stored and analysed in ThreatCloud. ThreatCloud provides real-time threat intelligence derived from hundreds of millions of sensors worldwide, over networks, endpoints and mobiles. ThreatCloud is the brain behind Check Point Software Technologies’ threat prevention power, combining big data threat intelligence with advanced AI technologies to provide accurate prevention to all Check Point Software Technologies customers.